Cybersecurity Services - Cybersecurity Risk Assessment
Protect your organization with NOXMON's comprehensive cybersecurity risk assessment. Our expert team identifies vulnerabilities, evaluates threats, and provides actionable insights to strengthen your security defenses.
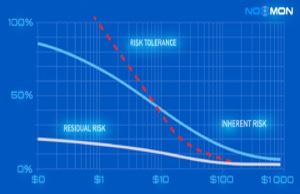
Comprehensive Security Evaluation
NOXMON's cybersecurity risk assessment provides organizations with a thorough evaluation of their current security posture. Using industry-leading methodologies including NIST Cybersecurity Framework, ISO 27001, and FAIR (Factor Analysis of Information Risk), we identify critical vulnerabilities and assess threat exposure across your entire technology infrastructure.
Our security experts conduct deep-dive assessments covering network security, endpoint protection, cloud infrastructure, data governance, identity and access management, and application security. We evaluate both technical controls and organizational processes to create a comprehensive risk profile.
The assessment includes vulnerability scanning, penetration testing, security architecture review, and policy evaluation. We provide detailed documentation of findings with risk ratings based on CVSS scoring and business impact analysis.
Our Assessment Process
Phase 1: Discovery & Planning
- Asset Inventory. Complete catalog of IT assets, systems, and data flows
- Threat Landscape Analysis. Industry-specific threat intelligence and attack vector assessment
- Compliance Requirements. Evaluation of regulatory and industry standards applicable to your organization
Phase 2: Technical Assessment
- Vulnerability Assessment. Automated and manual vulnerability identification across all systems
- Penetration Testing. Simulated attacks to test security controls and identify exploitable weaknesses
- Security Architecture Review. Evaluation of network segmentation, access controls, and defense-in-depth strategies
Phase 3: Risk Analysis
- Risk Quantification. FAIR-based analysis calculating potential financial impact of identified risks
- Business Impact Assessment. Evaluation of how security incidents could affect business operations
- Risk Prioritization. Risk matrix development based on likelihood and impact analysis
Phase 4: Reporting & Recommendations
- Executive Summary. High-level risk overview for board and executive leadership
- Technical Findings. Detailed vulnerability reports with remediation guidance
- Remediation Roadmap. Prioritized action plan with timelines and resource requirements
Assessment Deliverables
Comprehensive Risk Report
Detailed analysis of all identified risks with CVSS scores and business impact ratings
Remediation Roadmap
Prioritized action plan with timelines, costs, and resource requirements
Executive Dashboard
High-level metrics and KPIs for ongoing security posture monitoring
Compliance Gap Analysis
Assessment against relevant frameworks with specific compliance recommendations
Tell us about your project
Our offices
- Houghton
101 W. Lakeshore Dr.
Houghton, MI 49931
(212) 913-9184
info@noxmon.com - New York City
34 West 13th Street
New York, NY 10011
(212) 913-9184
info@noxmon.com